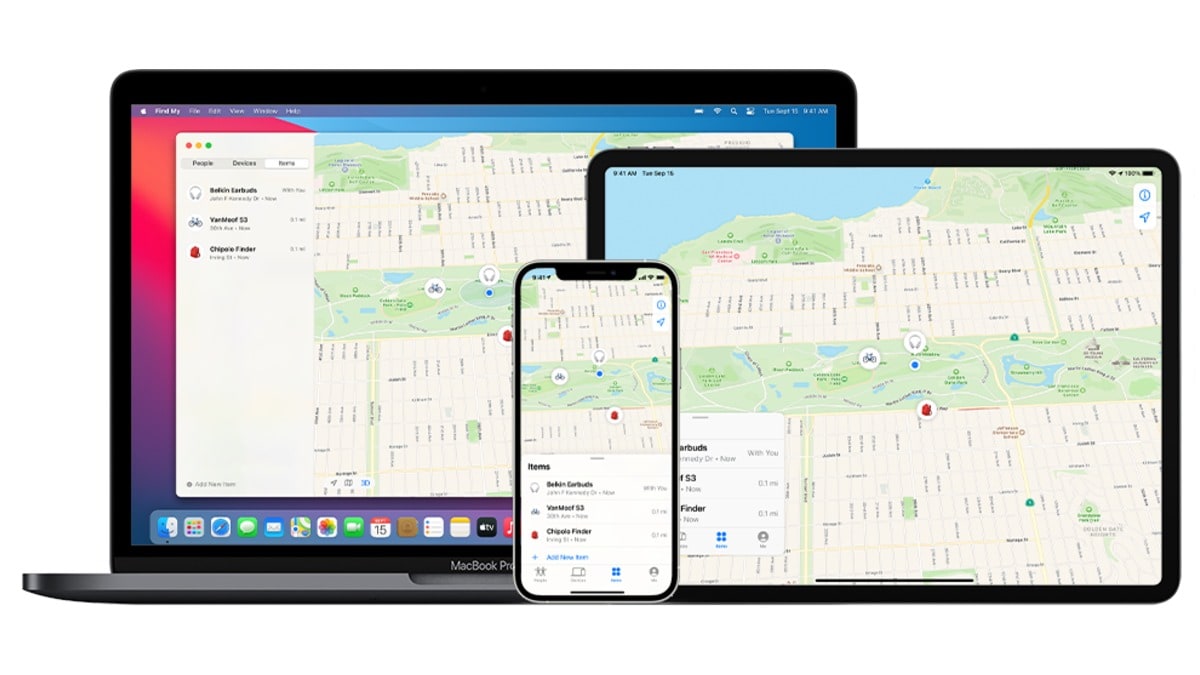
Apple’s Find My network can be used by hackers to track any device with Bluetooth connectivity by turning them into homing beacons like the company’s AirTag, according to researchers. A malicious user could trick Apple’s Find My network into tracking a smartphone, laptop, or any internet of things (IoT) device using its Bluetooth address, by tricking the network into thinking it is an AirTag. The exploit can be used to pinpoint the location of a device, or track it as it moves across a specific area.
Tricking the Find My Network Into Tracking Ordinary Bluetooth Devices
According to George Mason University researcher Junming Chen, the Apple’s Find My network contains a Bluetooth vulnerability that would allow a hacker to silently track a device by using its Bluetooth address. Dubbed ‘nRootTag’, this attack tricks the Find My network into thinking that a device is a lost AirTag.
A team of four researchers led by Chen discovered that the nRootTag attack could be used to identify the location of a Bluetooth connected device with an accuracy of 10 feet (3.05 metres). It could also be used to locate a larger object, such as an e-bike, and track it as it moved around a city. The team also highlighted that the flaw could also be misused to identify the location of smart locks that have been hacked, enabling attackers to easily find them.
While Apple protects user privacy on an AirTag by changing its Bluetooth address using a cryptographic key, this process requires elevated privileges. In order to circumvent this, the researchers used hundreds of GPUs to identify a key that is compatible with the Bluetooth address of a device, and making it adapt to the address.
The use of several rented GPUs offers an affordable method to quickly identify the location of a device “within minutes”. nRootTag has a 90 percent success rate, according to the researchers, who say that advertising companies could avoid the use of GPS and track or profile users with this technique.
While Apple’s network was designed to track the company’s own devices, the researchers were able to use nRootTag to track mobile devices, laptops, IoT devices, smart TVs, and even virtual reality (VR) headsets. They will present these findings at the USENIX Security Symposium in August.
The researchers contacted Apple about the security flaw in July 2024, and the company acknowledged their contribution in the release notes for iOS 18.2, which was released in December (see the Proximity section).
However, a proper fix for the issue — whenever it is released by Apple — would likely require an update to the Find My network, and might be delayed by users who defer the installation of software updates on their devices. The researchers state that the vulnerability in the Find My network could exist for years, until these outdated devices slowly “die out”.
Users can take some precautions to keep their devices safe from tracking, such as being judicious while granting apps access to the Bluetooth permission or making sure that their devices are up-to-date. The researchers also recommend the use of privacy focused operating systems that could potentially protect user privacy.